Ransomware is a form a malicious software that can be extremely costly to your business. A report from the cybersecurity firm Sophos found that the average cost to rectify the impact of a ransomware attack in 2020 was over $700,000 (USD) and doubles to over $1.4 million when including ransom payments to criminals.
Like most cybercrime, ransomware takes old methods of extortion to the digital realm, which reduces the time and cost to criminals, thus increasing the frequency of attacks.
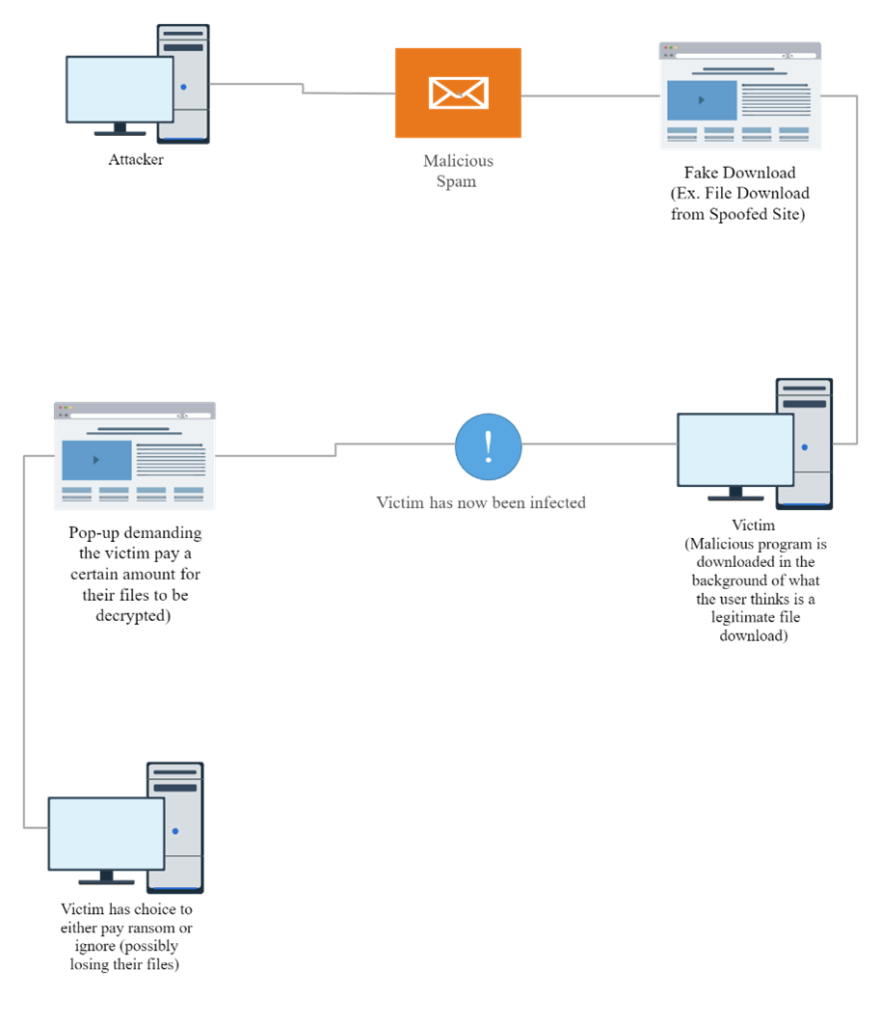
As the diagram below illustrates, a cybercriminal infect your computer with the malware that holds your data hostage, then demands that you pay a ransom, which may or may not reunite you with your data (cybercriminals are not known for keeping promises).
The history of ransomware dates to as early as 1989 with the AIDS Trojan attacks by Joseph Popp, but the majority of large-scale attacks have occurred in the last decade with Reveton, CryptoLocker, CryptoWall, Locky, WannaCry, Sodinokibi, Darkside, and Revil creating billions in losses for organizations in nearly every country.
The proliferation of ransomware tools, the increased use and value of cryptocurrency, economic instability, and the overall increase in data (and value of data) are making ransomware attacks easier to commit and more profitable by the day.
While sometimes fascinating, understanding concepts such as the Dark Web, hacker toolkits, and cryptovirology is not essential for business leaders.
What is essential in understanding the threat landscape. At the very least, you should be able to recognize threats, present a strong defense system, sense if you have been attacked, and know what to do if you are being attacked.
Ideally, you have a cybersecurity partner who has developed a strategy to minimize your risk profile.
Recognizing the Types of Ransomware
- Crypto: the most common type of ransomware, Crypto malware encrypts the data on your computer, and criminals typically ask for a ransom in cryptocurrency in exchange for the decryption keys.
- Lockers: target your operating system and lock you out of devices, making your data inaccessible.
- Mobileware: arrive via malicious mobile applications that lock your smartphone.
- Scareware: usually arrives via a web-browser pop-up claiming that your computer has a virus and demanding that you call a phone number or take action to remove the virus.
- Doxware: also known as leakware, cybercriminals encrypt or lock your computer and claim to have personal information that will be released online if you do not pay a ransom.
- RaaS: an acronym for “Ransomware as a service,” RaaS is a ransomware at scale with large criminal organizations committing crimes on behalf of their clients for a percentage of the ransom payment.
Building a Ransomware Defence
Cybercriminals choose their victims carefully. Just as the burglar is more likely to break into the house with a bag of cash on the windowsill than the house with a gate, alarm system, and guard dog, cybercriminals are more likely to target those with weak defences and valuable data. Consider the following questions:
- Where are you located? If you are in North America, Australia, New Zealand, or Western Europe, you are seen as a high-value target due to your wealth and widespread use of personal computers.
- What does your cybersecurity team look like to an outsider? If there is little indication online that you have a cybersecurity strategy in place, you may look like an easy target for criminals.
- How valuable is your data? If companies in your industry are known to possess intellectual property, trade secrets, payment information, confidential client data, or legal data, criminals will perceive you as a high value target both in terms of the money they can get by selling your data and what you will be willing to pay to retrieve it.
There are measures that should always be in place to protect your business, no matter your business’ size or risk profile:
- Implement a Data Backup Strategy: an intelligent data backup plan with externally hosted, redundant copies of your data that can be quickly restored is the best tool against ransomware attackers.
- Implement a Software Update and Patch Policy: cybercriminals rely on known exploits in operating systems and cybersecurity software as attack vectors. By keeping your systems up-to-date, you are eliminating attack vectors.
- Establish Policies, Practices, and Procedures: Your role as a business leader is to make cybersecurity a part of your company’s culture. This means establishing policies, practices, and procedures, communicating your vision to your employees, educating your employees with the help of your cybersecurity partners, rewarding good cybersecurity behaviour, and mentoring employees who have not yet embraced the culture.
Sensing a Ransomware Attack
There are key indicators that your business may have been attacked with ransomware. Your cybersecurity partner should be monitoring your systems for these warning signs:
- Suspicious Emails: Cybercriminals often begin their attacks by sending phishing emails. These are a form of social engineering that appear as though from a legitimate sender, but with a malicious attachment or link that once clicked by a user, provide an entry point to your network.
- Unexpected Network Scanners: Cybercriminals attempt to gain access to one computer, then move through your network to find domain rights, and use that information to gain access to additional computers.
- Unauthorized Access to Active Directory: Cybercriminals collect information about your business’ users, groups, and computers, then map pathways to escalate privileges to domain administrator and gain control of your systems.
- Software Removal Programs: After the cybercriminals gains administrative privileges, their next step is usually to remove or disable security software like antivirus protections. Software removal programs are a sure sign that an attack is imminent and that your cybersecurity partners must act quickly.
Responding to a Ransomware Attack
In the event that you are the victim of a ransomware attack, you typically have two options:
- Pay the Ransom: this is usually the costliest option, and again, payment is no guarantee that you will retrieve your data. The other problem with paying cybercriminals is that you are rewarding crime and incenting future crimes.
- Try to Remove the Malicious Software: by removing all connections to the internet, scanning all machines for malicious software, running a decryption tool, and restoring your external data backup, you may be able to remove, recover, and reset your infrastructure to the pre-attack status quo. Remove all internet connections to disable the ransomware from spreading.
Ransomware is a major cybersecurity challenge for businesses, but you can prevent it with leadership, strategy, and the right technical partners.

